
In present context, it is very essential to maintain security and integrity of cloud infrastructure. And Amazon Web Services (AWS) provides a comprehensive set of tools and services to protect system against potential vulnerabilities and attacks. System hardening on AWS involves implementing a range of security measures to protect data and resources. Some of the key strategies and best practices for hardening AWS infrastructure are as follows:
Employing Multi-Factor Authentication (MFA): One of the major step in securing AWS environment is enabling Multi-Factor Authentication. MFA adds an extra layer of security to AWS accounts by requiring an additional form of authentication, such as a code from a mobile app. To enable MFA, simply navigate to (Identity and Access Management) console, select the appropriate user, and follow the instructions to activate MFA.
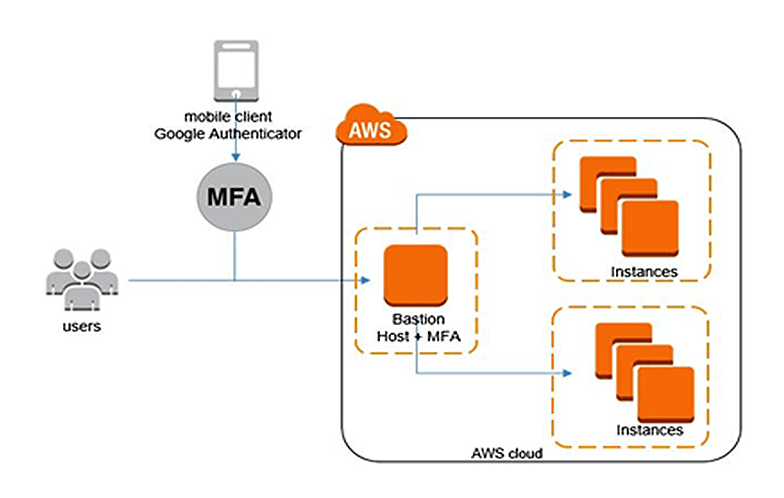
Assigning Least Privilege Access with IAM Roles: AWS Identity and Access Management roles provide a secure and scalable way to manage AWS services and resources. We can control access at granular level and should avoid using long-term access keys whenever possible.

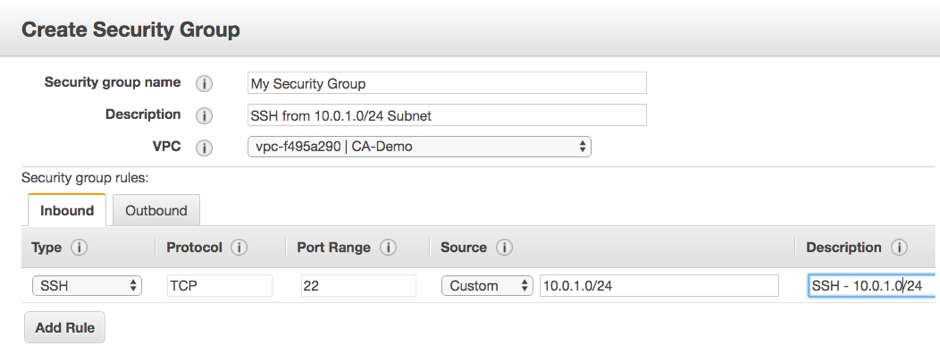
Securing Network Access with Security Groups: Security groups act as virtual firewalls that control inbound and outbound traffic to AWS instances. By defining explicit rules, we can limit access to specific ports, IP ranges or protocols. It is very important to regularly review and update our security group rules to ensure only necessary traffic is allowed. And adding another security level by applying Network Access Control List (NACL) at subnet level while configuring Virtual Private Cloud (VPC).
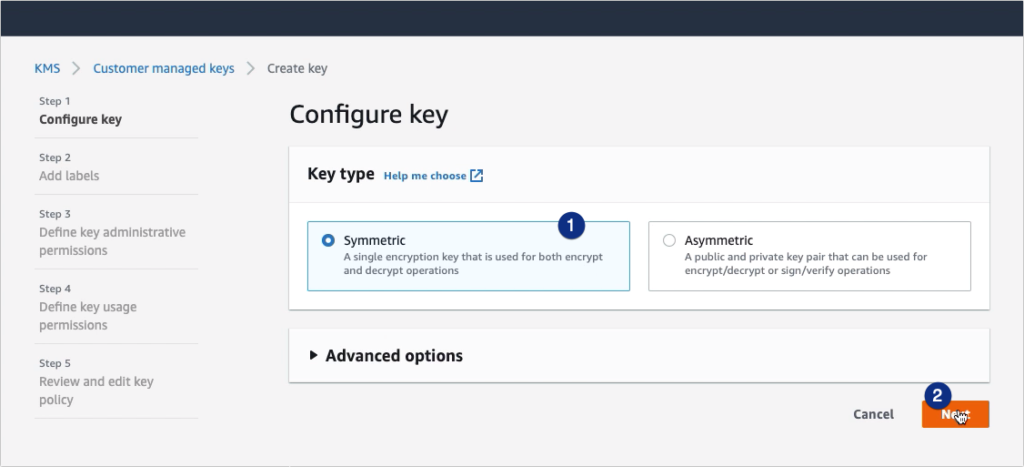
Implementation of Encryption: Protection of data while at rest and in transit is another essential to prevent unauthorized access to AWS resources. AWS Key Management Service(KMS) enables us to manage and control encryption keys. We can encrypt data on Amazon S3, EBS volumes, RDS databases, and other services using KMS.
AWS WAF and Shield for DDoS Protection: To defend against Distributed Denial of Service (DDoS) attacks, AWS provides two essential services known as AWS Web Application Firewall and AWS Shield. AWS WAF allows us to define rules to filter out malicious traffic and protect our web applications. Whereas, AWS Shield provides automatic protection against volumetric, state-exhaustion, and application layer DDoS attacks.
Similarly, AWS Trusted Advisor gives us recommendation to follow AWS best practices and evaluates our account by using checks. Likewise, AWS Guard Duty is a threat detection service and CloudTrail offers auditing, security monitoring, and operational troubleshooting by tracking user activity and API usage.
Therefore, by applying these best practices, we can significantly enhance the resilience of our AWS cloud environment.

Leave a Reply