There has been a massive increase in the number of businesses relying on cloud computing, and the security of their cloud infrastructure is very essential. One of the major way to securing the cloud environment is through network hardening. In this blog, I will explore various best practices and techniques for AWS network hardening to ensure the protection of data and resources. The key areas of discussion will be network access control, encryption, traffic monitoring, and more.
Implementing a Multi-Layered Security Approach: Securing AWS network requires a multi-layered strategy of defense which begins by creating separate security groups to segment the resources. Each security group should have explicit inbound and outbound rules to minimize the exposure of your resources to unnecessary risks.
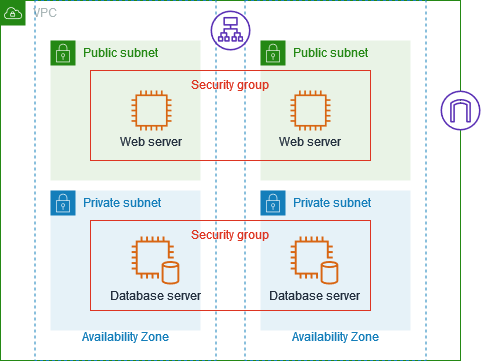
Leveraging Virtual Private Cloud (VPC): AWS Virtual Private Cloud (VPC) enables to create an isolated network environment within the AWS cloud. To harden the network, following practices can be considered:
Designing Proper VPC: Planning the VPC with different subnets for various types of resources, ensuring appropriate separation and isolation.
Utilization of Network Access Control Lists (NACL): NACL acts as a firewall at the subnet level, controlling inbound and outbound traffic. It helps us to configure allow or deny protocols, ports and IP ranges.
Strengthening Network Access: Controlling access to your network is very critical and here are some recommended practices:
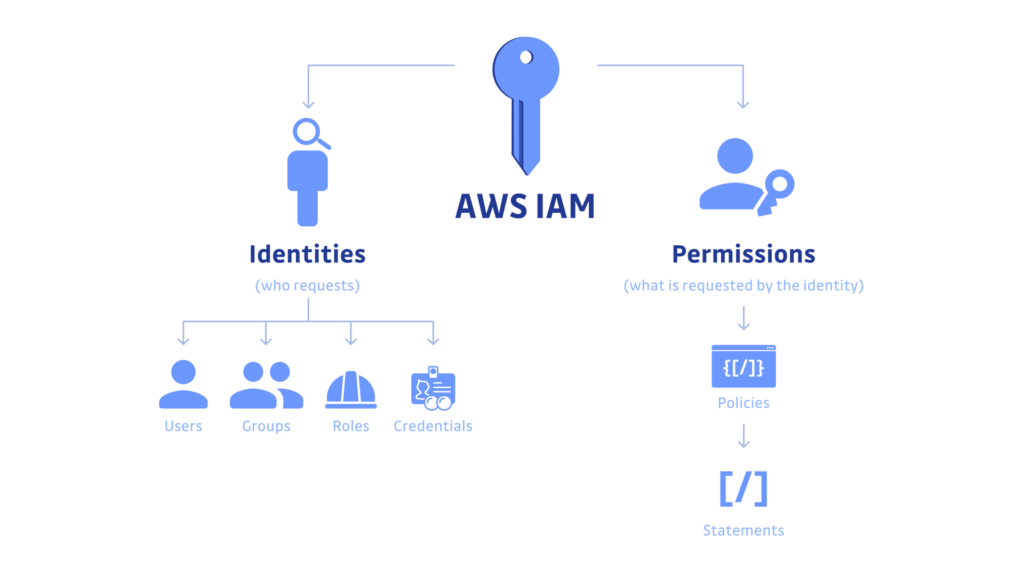
Use of AWS Identity and Access Management (IAM) service: Implement access control using IAM roles and policies to grant the least privilege principle.
Secure network gateways: Ensuring the Internet and VPN gateways are securely configured with appropriate routing and access control.
Encryption for Data Protection: Data encryption plays a crucial role in securing the network. Following approaches can be considered:
Implement Transport Layer Security (TLS) using AWS Certificate Manager (ACM) service : Enable SSL/TLS encryption for communication over the internet to protect data in transit.
Employ AWS Key Management Service (KMS): Use KMS to manage and control the encryption keys for your sensitive data stored in AWS services like S3 or RDS.
Continuous Monitoring and Auditing: Regular monitoring and auditing are essential for detecting and mitigating potential threats and following practices can be considered for the same:
Enable AWS CloudTrail: AWS CloudTrail provides a detailed log of API calls made within your AWS account, allowing you to monitor and investigate any suspicious activities.
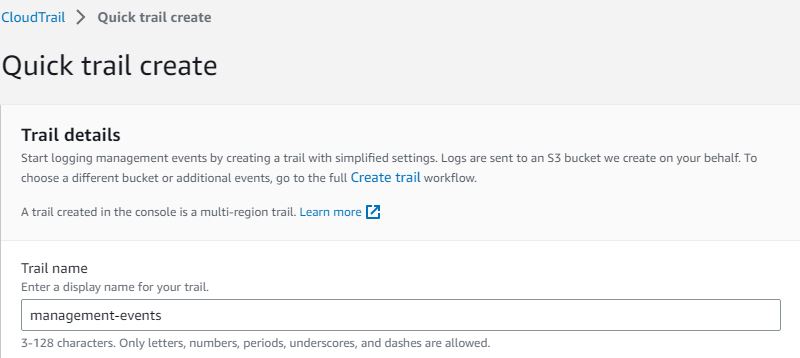
Implement AWS Guard Duty: Guard Duty is a threat detection service that uses machine learning and anomaly detection algorithms to identify potential malicious activities within your AWS environment.
Therefore, network hardening is an ongoing process, and it is crucial to stay updated with the latest security features and vulnerabilities. Safeguarding the network ensures integrity, confidentiality, and availability of valuable data and resources in the cloud.
Leave a Reply